A digital signature in its simplest description is a hash (SHA1, MD5, etc.) of the data (file, message, etc.) that is subsequently encrypted with the signer’s private key. Since that is something only the signer has (or should have) that is where the trust comes from. EVERYONE has (or should have) access to the signer’s public key.
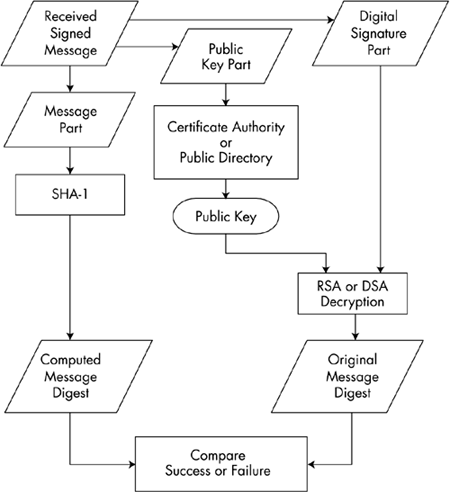
So, to validate a digital signature, the recipient
- Calculates a hash of the same data (file, message, etc.),
- Decrypts the digital signature using the sender’s PUBLIC key, and
- Compares the 2 hash values.
Sender – Alice is sending a digitally signed but not encrypted message to Receiver – Bob
- Sender generates a message digest of the original plaintext message using a secure hash function like SHA3-512.
- Sender then encrypts the message digest using her private key. The output is the digital signature.
- Sender appends the digital signature to the plaintext message.
- Sender then sends the appended message to Receiver. Sender sends digital signature + Plain Text Message + Certificate with Public Key
- Receiver removes the digital signature from the appended message and decrypts it with the public key of Sender.
- Receiver calculates the hash of the plaintext message with SHA3-512.
- Receiver then compares the decrypted message digest he received from Sender with the message digest Receiver computed. If the two digests match, he can be assured that the message he received was sent by Sender.
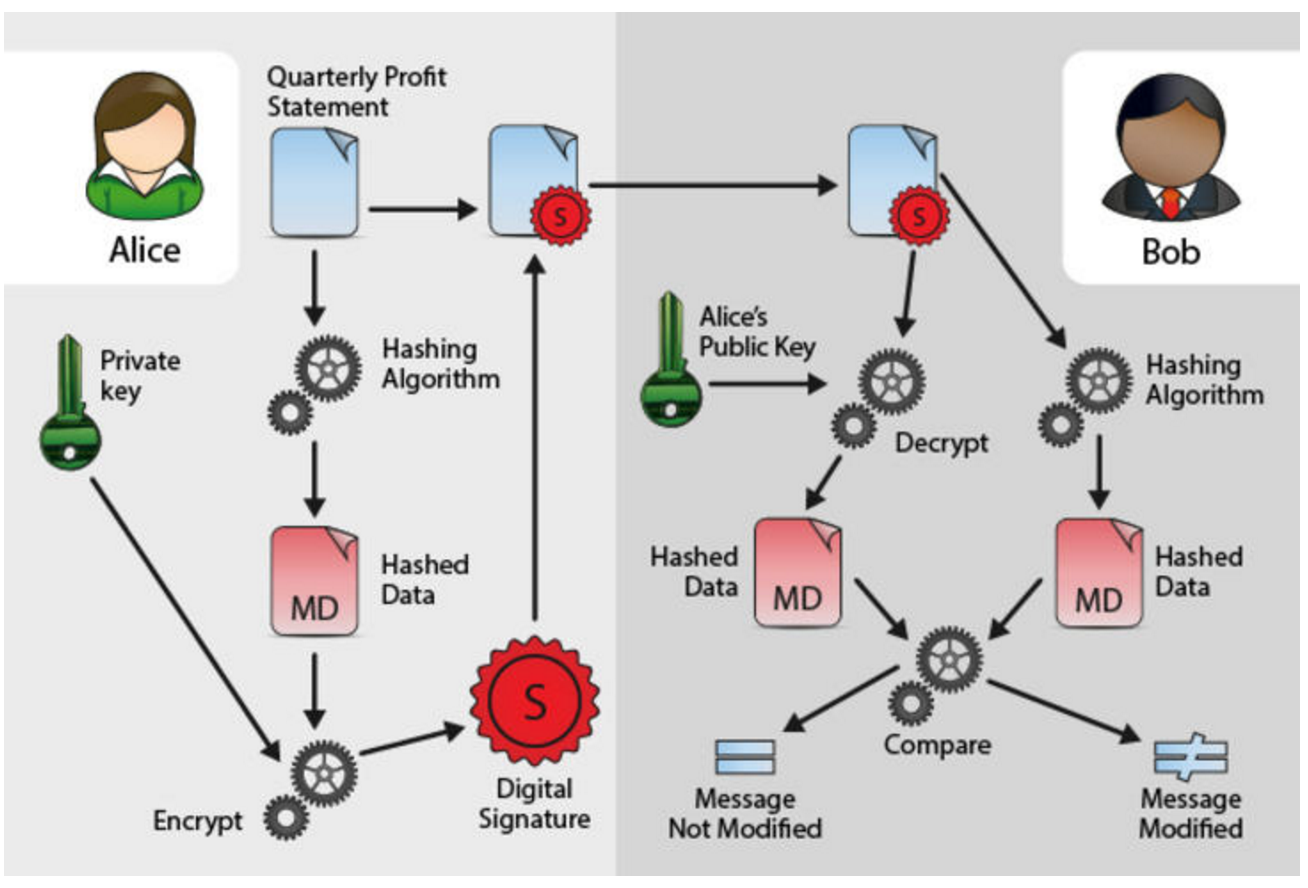
The digital signature process does not provide any privacy by itself. It only ensures that the cryptographic goals of authentication, integrity, and nonrepudiation are met. If Sender wants to ensure the privacy of her message to Receiver, she could encrypt the appended message generated in step 3 with the public key of Receiver. Receiver then would need to first decrypt the encrypted message with his private key before continuing with step 5.
What Sender Does?
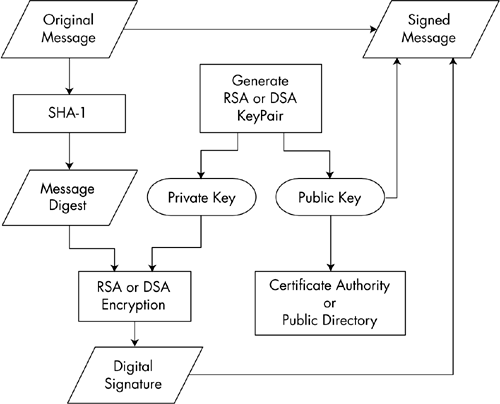
Note: In the above step the hash is encrypted digitally signed using private key.In the side of the receiver public key should be used to decrypt hash for verification
What Receiver Does?