- What is a Cipher?
A cipher transforms data by processing the original, plaintext characters (or other data) into ciphertext, which should appear to be random data - What is Message Digest? Why we need Message Digest?
A message digest is a cryptographic hash function containing a string of digits created by a one-way hashing formula. Message digests are designed to protect the integrity of a piece of data or media to detect changes and alterations to any part of a message.This term is also known as a hash value and sometimes as a checksum.Message digests are encrypted with private keys creating a digital signature. This results in a type of validation ensuring that the appropriate user is accessing protected information. Message digests protect one-way hash algorithms taking random data and transmitting a set length hash value. - What is role of Hasing in Security? Hashing helps in preventing or analyzing file tampering. The original data will generate a hash which is kept with the data. The data and the hash are sent together, and the receiving party checks that hash to see if the data has been compromised. If there were any changes to the data, the hash wont match.
- What is Secure Hash Algorithm (SHA)?Secure Hash Algorithms, also known as SHA, are a family of cryptographic functions designed to keep data secured. It works by transforming the data using a hash function: an algorithm that consists of bitwise operations, modular additions, and compression functions. The hash function then produces a fixed-size string that looks nothing like the original. These algorithms are designed to be one-way functions, meaning that once they’re transformed into their respective hash values, it’s virtually impossible to transform them back into the original data. A few algorithms of interest are SHA-1, SHA-2, and SHA-3, each of which was successively designed with increasingly stronger encryption in response to hacker attacks. SHA-0, for instance, is now obsolete due to the widely exposed vulnerabilities.
- What does MessageDigest getInstance() does?
MessageDigest class provides a method named getInstance(). This method accepts a String variable specifying the name of the algorithm to be used and returns a MessageDigest object implementing the specified algorithm.Create MessageDigest object using the getInstance() method as shown below.
MessageDigest md = MessageDigest.getInstance("SHA-256");After creating the message digest object, you need to pass the message/data to it. You can do so using the update() method of the MessageDigest class, this method accepts a byte array representing the message and adds/passes it to the above created MessageDigest object.
md.update(msg.getBytes());
You can generate the message digest using the digest() method od the MessageDigest class this method computes the hash function on the current object and returns the message digest in the form of byte array.Generate the message digest using the digest method.
byte[] digest = md.digest();
- Could I use Public and Private Keys Inversely?
Yes. The keys work inversely to each other. Encrypted something with your public key? Decrypt it with your private key. Conversely, if you encrypt something with your private key, you decrypt it with your public. Such is the nature of asymmetric cryptography. - What is Symmetric and Asymmetric Keys?
Symmetric just means that the same key is used to encrypt/decrypt. Asymmetric means that one key encrypts and a different key decrypts (and that the reverse is also true).#Creating a key Pair openssl genrsa -out private.pem 1024 openssl rsa -in private.pem -out public.pem -pubout #Encrypt with public & decrypt with private openssl rsautl -encrypt -inkey public.pem -pubin -in message.txt -out message.ssl openssl rsautl -decrypt -inkey private.pem -in message.ssl -out message.txt #Encrypt with private & decrypt with public openssl rsautl -sign -inkey private.pem -in message.txt -out message_enc_priv.ssl openssl rsautl -inkey public.pem -pubin -in message_enc_priv.ssl -out message_priv.txt
- In the above example, you could see the public key is genarated first followed by generation of private key. Any idea why it is so?
elliptic curve cryptography (also called “elliptic curve multiplication”) is the answer to the question. Elliptic curve cryptography is the mathematical relationship that makes the following conditions possible:- A public key can be mathematically generated from a private key
- A private key cannot be mathematically generated from a public key (i.e. “trapdoor function”)
- A private key can be verified by a public key
a public/private keypair is created using elliptic curve cryptography, which by nature, creates a public and private key that are mathematically linked in both directions, but not mathematically derived in both directions.
- is JWT secured?
JWT are used for authorization and not authentication.Information in the payload of the JWT is visible to everyone. There can be a “Man in the Middle” attack and the contents of the JWT can be changed. So we should not pass any sensitive information like passwords in the payload. We can encrypt the payload data if we want to make it more secure. If Payload is tampered with server will recognize it. - What is Resource and Authorization Server? Authorization server is the one which issues the JWT after authentication. Resource server is the one which authorizes User every time using JWT while accesing resource
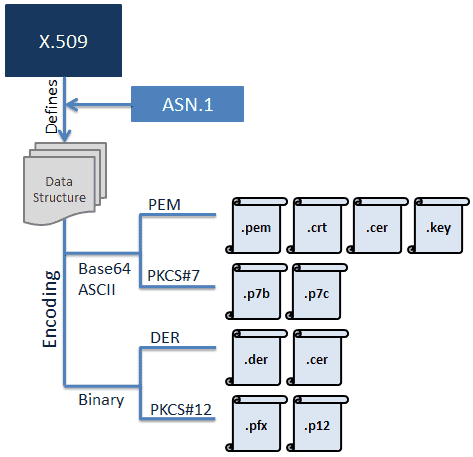
- What does .pem file contains?
PEM stands for Privacy-Enhanced Mail. A PEM file may contain anything including a public key, a private key, or both, because a PEM file is not a standard. In effect PEM just means the file contains a base64-encoded bit of data.
Typically a PEM file contains a base64 encoded key or certificate with header and footer lines of the form —–BEGIN—– and —–END —-. Over time there have evolved many possibilities for , including private keys, public keys, X509 certificates, PKCS7 data, files containing multiple certificates, files containing both the private key and the X509 certificate. - What is CSR and CRT(or)CER?
Certificate Signing Request contains information such as the public key and common name required by a Certificate Authority to create and sign a certificate for the requester, the encoding could be PEM or DER. These get signed by the CA and a certificate is returned. The returned certificate is the public certificate (which includes the public key but not the private key). Since the public key is signed by CA, the CA is confident the one who has sent for signing is the only one who has access to private key. - What is PKIX?
PKIX is an IETF (Internet Engineering Task Force) working group with the goal of supporting public key infrastructures based on X.509 on the Internet.X.509 certificate is a digital certificate based on the widely accepted International Telecommunications Union (ITU) X.509 standard, which defines the format of public key infrastructure (PKI) certificates. They are used to manage identity and security in internet communications and computer networking