When the client communicates with the server over HTTPS either browser or REST call, the server doesn’t care who the client is, as long as they have the correct credentials. This is what happens in Login forms(Asymmetric communication followed by Symmetric Communication).
Two-way SSL is used for places where you only want the server to accept connections from a restricted number of users. It helps to mitigate the risk of fraud in online transactions. Two-way SSL authentication (also known as “mutual authentication”, or “TLS/SSL with client certificates”) where two parties authenticate
each other through verifying provided digital certificates, so that both parties are assured of the other’s identity.
In One-way SSL, where the browser (the client) establishes an SSL connection to a secure web site and the server’s certificate is checked, creating SSL authentication in RESTful web services. The browser either relies on itself or the operating system providing a list of certs that have been designated as trusted Certificate Authorities (CA).
In context to java, Java Key Store is used to store the certs and keys.It must be password protected and entries in it must have an “alias” that is unique. If an alias is not specified, “mykey” is used by default.
KeyStores provide credentials, TrustStores verify credentials.Clients will use certificates stored in their TrustStores to verify identities of servers. They will present certificates stored in their KeyStores to servers requiring them.
The JDK ships with a tool called Keytool. It manages a JKS of cryptographic keys, X.509 certificate chains, and trusted certificates.
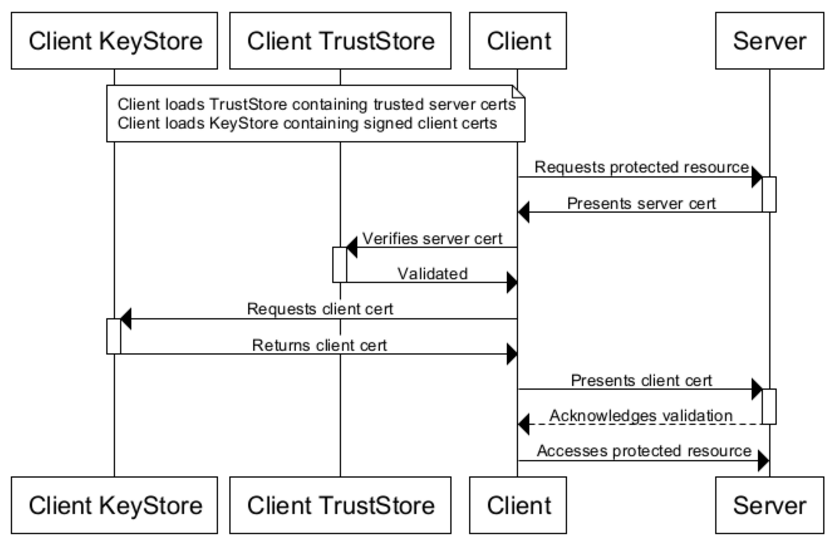
//Importing a truststore which could be used by client for server certificate verification >> keytool -import -v -trustcacerts -keystore client_truststore.jks -storepass apassword -alias server -file foo.snaplogic.com.cert //Importing a keystore which could be used by client when server asks of identity certificate >> keytool -importkeystore -srckeystore client-certificate.p12 -srcstoretype pkcs12 -destkeystore client_keystore.jks -deststoretype jks -deststorepass apassword // Viewing list of servcer certificates in Client Truststore >> keytool -list -v -keystore client_truststore.jks
We can now complete configuration of the REST SSL Account by uploading our client_truststore.jks and client_keystore.jks KeyStore files
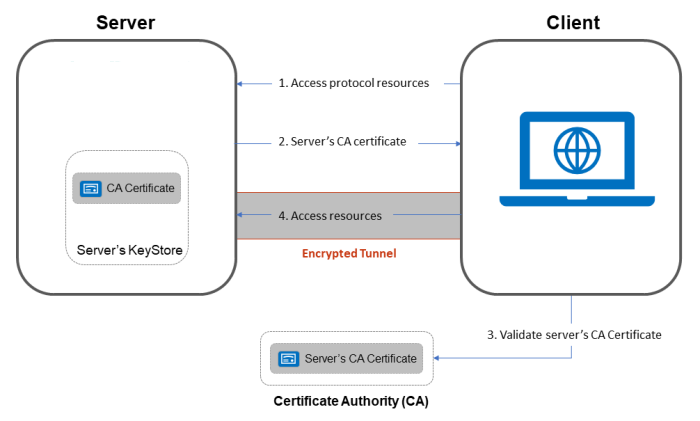
One way SSL
- Client requests for some protected data from the server on HTTPS protocol. This initiates SSL/TLS handshake process.
- Server returns its public certificate to the client along with server hello message.
- Client validates/verifies the received certificate. Client verifies the certificate through certification authority (CA) for CA signed certificates.
- SSL/TLS client sends the random byte string that enables both the client and the server to compute the secret key to be used for encrypting subsequent message data. The random byte string itself is encrypted with the server’s public key.
- After agreeing on this secret key, client and server communicate further for actual data transfer by encrypting/decrypting data using this key.
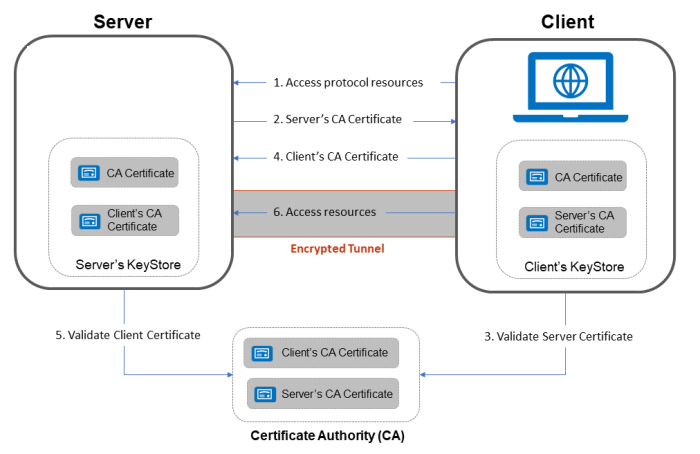
Two way SSL
- Client requests a protected resource over HTTPS protocol and the SSL/TSL handshake process begins.
- Server returns its public certificate to the client along with server hello.
- Client validates/verifies the received certificate. Client verifies the certificate through certification authority (CA) for CA signed certificates.
- If Server certificate was validated successfully, client will provide its public certificate to the server.
- Server validates/verifies the received certificate. Server verifies the certificate through certification authority (CA) for CA signed certificates.
- After completion of handshake process, client and server communicate and transfer data with each other encrypted with the secret keys shared between the two during handshake.